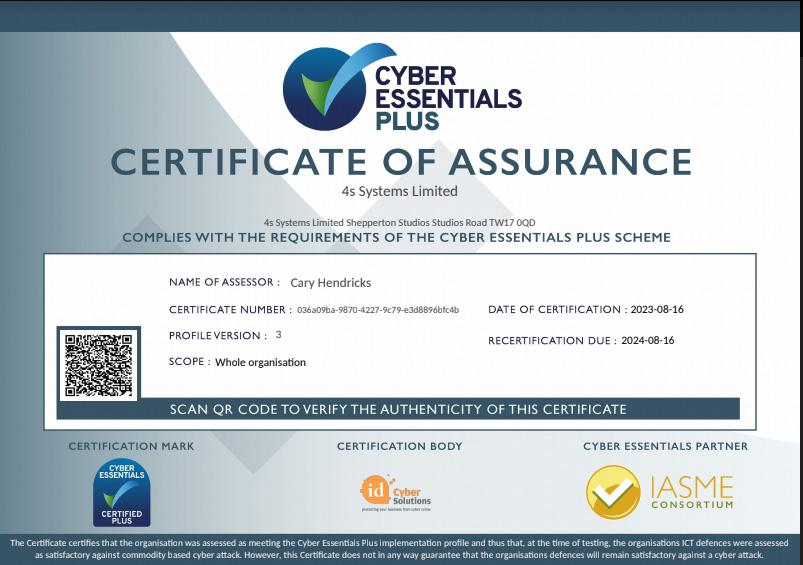
by Johnny Konstants | Sep 1, 2023 | Security
Cybersecurity is an essential aspect of any organisation’s information technology (IT) infrastructure. In today’s digital world, businesses need to take proactive measures to safeguard their IT systems and data from cyber threats. One way of achieving this...

by Johnny Konstants | Aug 4, 2023 | IT Maintenance
Your businesses will benefit from having a reliable partner to manage their IT infrastructure in both the short run and the long run. A managed IT service provider offers many substantial benefits to help support and develop your business. Expertise and...

by Johnny Konstants | Jul 17, 2023 | IT Maintenance
As your business navigates an ever-changing IT landscape, having access to trusted management of your information technology (IT) infrastructure is imperative. However, your business may lack the expertise, time, or resources to handle these IT needs internally. A...

by Johnny Konstants | Jul 7, 2023 | IT Maintenance
As your business navigates an ever-changing IT landscape, having access to effective management of your information technology (IT) infrastructure is imperative. However, your business may lack the expertise, time, or resources to handle these IT needs internally. A...
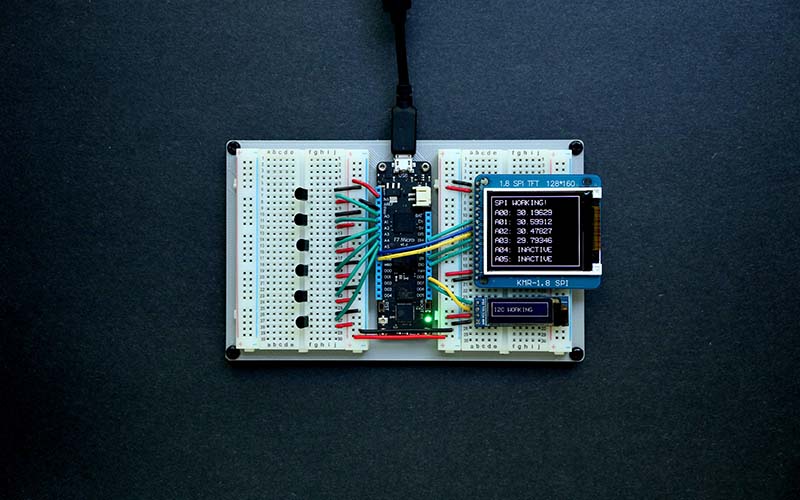
by Johnny Konstants | Jun 4, 2023 | Security
IoT Security With the rise of Internet of Things (IoT) devices, the need for strong security measures has become increasingly important. IoT devices are vulnerable to cyber-attacks, which can cause significant harm to individuals and organisations. In this blog, we...






